Sven Krasser's Blog
Musings on technology, security & sundries
-
USB Mini Media Keyboard
For my latest electronics project, I’ve built a small USB keyboard input device for media control. The final version has three keys: play/pause, previous track, and next track. In addition, a rotary encoder allows adjusting the volume (or mutes sound when pressed). This is also my first project involving a custom circuit board — my previous electronics projects mainly involved breadboards of varying sizes.
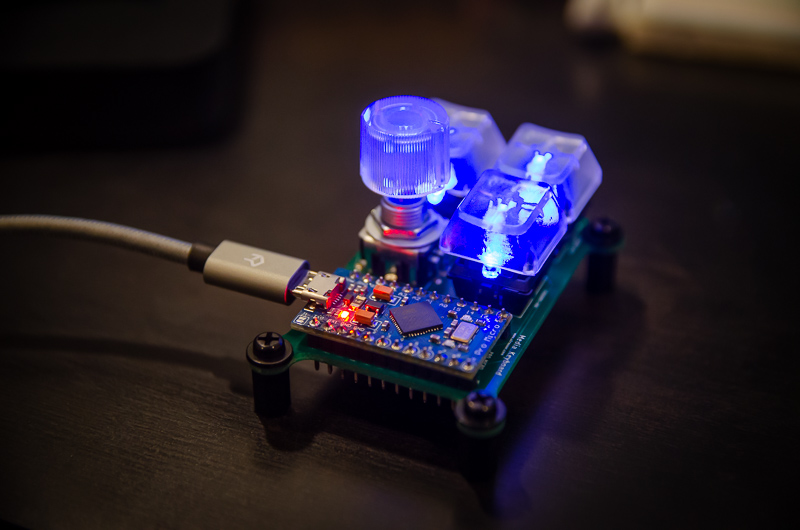
-
Homebrew Computer: Adding a 6522 VIA
In my last post, I wrote about my first steps towards a 6502-based homebrew 8-bit computer. Since then I’ve added a 6522 Versatile Interface Adapter (VIA). More specifically, it is a W65C22S. The VIA has a number of functionalities (after all, it makes a claim to being versatile).
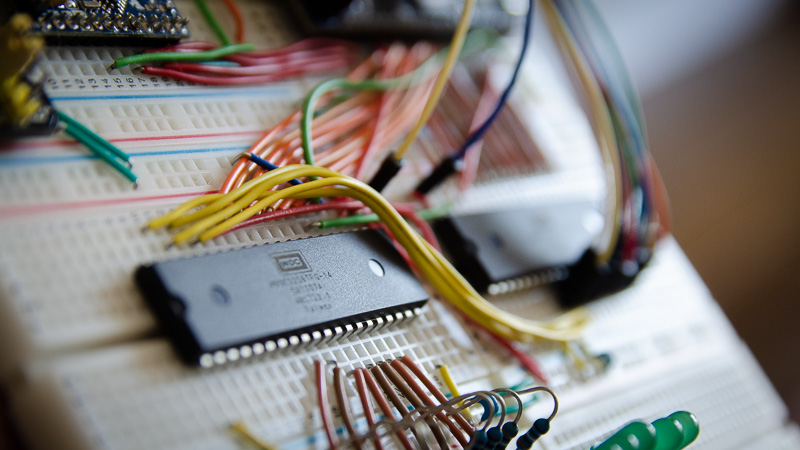
-
Simple Homebrew 6502 Computer
After completing my VGA Generator project a while back, I’ve embarked on a new electronics project: building a simple 6502-based homebrew 8-bit computer on a breadboard. There are a bunch of similar projects online from which to draw ideas. Some projects set constraints such as only using contemporary parts of the 8-bit era, no FPGAs, no microcontrollers etc. In my case, I opted instead to keep the constraints minimal and the project simple.
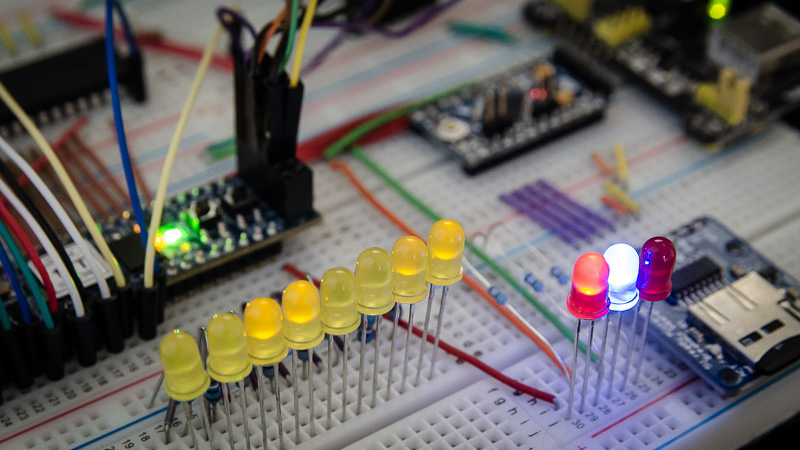
-
OA-9 Launch
This past Monday morning, the OA-9 mission launched from Wallops Island to deliver supplies to the ISS. I was lucky to be able to watch the launch from the launch facility’s viewing area alongside the JPL RainCube team whose spacecraft was onboard the rocket.
-
Black Hat 2017, Machine Learning, Electricity
This year, Black Hat celebrated its 20th anniversary. The keynote moved to a packed Mandalay Bay Arena with some noteworthy production values. On the content side, the conference featured again various Machine Learning (ML) themed talks. Most noteworthy, the Revoke-Obfuscation talk discussed utilizing ML as tool to detect Powershell obfuscations without buzzword abuse (read the abstract).
-
Practical Machine Learning in Information Security
Last week, I gave a talk at Security Data Science Colloquium hosted by Microsoft on their campus in Redmond. You can find my slides below.
-
Goodbye, Mac
Over the past year, I came across quite a few blog posts of people that moved back to Windows from Mac. Evidently, it’s time for my own. If that sort of anecdote doesn’t interest you, look at some other posts around here. Otherwise, here we go…
-
Machine Learning and Anti-Malware
It has been an exciting month at CrowdStrike, especially for the Data Science Team as we released our anti-malware engine to Google’s VirusTotal service last week—the first fully machine learning-based engine to be integrated on VirusTotal. The engine shared is part of the larger Falcon Host product; the main intent is to provide a pre-execution static analysis capability.
I’ve posted some technical details to the CrowdStrike blog, and CrowdStrike’s CEO George Kurtz shared his thoughts on this milestone as well.
-
Machine Learning Misconceptions
In cybersecurity, machine learning is frequently described as a panacea solving all our problems. In reality, things are of course a bit more complicated. Machine learning can help extracting more value from data, but a prerequisite is to have quality data to being with—at the right scale and the right scope—which is not always a given in the security space.
I’ve teamed up with Dmitri to share some thoughts on this topic over at Information Management. Take a look.
-
VGA from Scratch (Part 2)
After creating a basic VGA signal using discrete CMOS logic chips in Part 1, my goal was to get something more interesting onto the screen. Long story short, after adding thirty-something additional ICs, this is the outcome: